Unggulan
- Dapatkan link
- X
- Aplikasi Lainnya
Vpn Over Tor : Best VPN for Tor Browser in 2020 - Our Top 5 Picks : With that in mind, we look into which is the best available on all major platforms, nordvpn features specialized onion over vpn servers that allow you to access the tor network using any browser.
Vpn Over Tor : Best VPN for Tor Browser in 2020 - Our Top 5 Picks : With that in mind, we look into which is the best available on all major platforms, nordvpn features specialized onion over vpn servers that allow you to access the tor network using any browser.. Generally speaking, we don't recommend using a vpn with tor unless you're an advanced user who knows how to configure both in a way that doesn't compromise your privacy. Defend yourself against tracking and surveillance. A vpn adds a layer of encryption and routes traffic it has a tor over vpn option which means your traffic is automatically routed through the tor network. Learn all there is to know about this method of connection here! Without the vpn the tor guard (or bridge) is connecting to your isp's assigned ip address.
How to use tor browser with a vpn. But if you use tor over vpn, the vpn will shield your data on its way to the entry node. If you have been trying to access the dark web, it would be a bummer if everyone on the web can easily identify your whereabouts. Also, your isp can see that you're using tor, which may make it suspicious or make you a target. Using tor in conjunction with a virtual private network (vpn) can hide the fact you're using tor at all.

Additionally, using tor over vpn gives you access to onion sites like those operated by protonmail, facebook, and the new york times, among many others.
The additional issue of vpn over tor is that this method requires a. However, there are also disadvantages of using tor over vpn. Also, your isp can see that you're using tor, which may make it suspicious or make you a target. Both have their advantages when it comes to both security and usability. So it does not matter if the exit node can see which websites you are visiting; Using tor with a vpn is a good way to add another layer of security. But, when talking about tor vs vpn, how much do you really know? We will not be discussing this technique in detail because tor bridge relays are generally considered a better way to achieve that goal.) As far as we know, only airvpn offers this capability. Vpn over tor is more difficult to set up because it requires configuration on the vpn server. Cyberghost is compatible with tor and other proxy services and makes your. Tor over vpn is a method to make your connection absolutely anonymous. Connecting to tor through a vpn generally offers higher security, while connecting t.
When it comes to ensuring that our personal information and online activity remains private, vpns and tor to keep your privacy secure, you should avoid sending private messages and other sensitive information over your connection. Also, your isp can see that you're using tor, which may make it suspicious or make you a target. It's impossible to explain how onion over vpn works without touching how each component works separately. However, there are also disadvantages of using tor over vpn. In this guide, we make recommend the best vpns for tor and give you information and some helpful tips on using a vpn over onion.
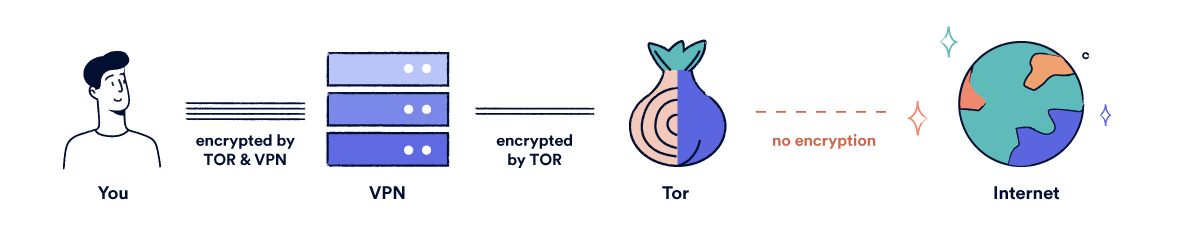
Also, your isp can see that you're using tor, which may make it suspicious or make you a target.
| can i use a vpn with tor? In this guide, we make recommend the best vpns for tor and give you information and some helpful tips on using a vpn over onion. Both have their advantages when it comes to both security and usability. So it does not matter if the exit node can see which websites you are visiting; Also, your isp can see that you're using tor, which may make it suspicious or make you a target. A vpn and tor are very different beasts, but they are both privacy technologies with a great deal of overlap in function. Although you've likely heard about tor browsers being able to hide your identity, you still need a much powerful tool like a tor over vpn to actually encrypt your internet traffic. But if you use tor over vpn, the vpn will shield your data on its way to the entry node. While protonvpn supports both tcp and udp traffic, tor only supports tcp. Vpn over tor is more difficult to set up because it requires configuration on the vpn server. If you have been trying to access the dark web, it would be a bummer if everyone on the web can easily identify your whereabouts. A vpn adds a layer of encryption and routes traffic it has a tor over vpn option which means your traffic is automatically routed through the tor network. I looked closely at every vpn's overall security features, including encryption, authentication keys.
Without the vpn the tor guard (or bridge) is connecting to your isp's assigned ip address. Tor over vpn is a method to make your connection absolutely anonymous. Using tor with a vpn is a good way to add another layer of security. Using tor in conjunction with a virtual private network (vpn) can hide the fact you're using tor at all. When it comes to ensuring that our personal information and online activity remains private, vpns and tor to keep your privacy secure, you should avoid sending private messages and other sensitive information over your connection.

With over 2900 servers in 59 countries, cyberghost is a popular vpn client.
It comes down to what you are trying to protect. A vpn adds a layer of encryption and routes traffic it has a tor over vpn option which means your traffic is automatically routed through the tor network. With the entry node oblivious to your ip address, your identity is protected from start to finish. While protonvpn supports both tcp and udp traffic, tor only supports tcp. If you have been trying to access the dark web, it would be a bummer if everyone on the web can easily identify your whereabouts. So it does not matter if the exit node can see which websites you are visiting; We will not be discussing this technique in detail because tor bridge relays are generally considered a better way to achieve that goal.) With over 2900 servers in 59 countries, cyberghost is a popular vpn client. Vpn over tor also protects malicious exit nodes, which is another plus. When using tor over vpn (start vpn, then tor), choose wisely who your vpn is. The vpn over tor method is considered more difficult to use as you must configure some users suggest that the vpn over tor method doesn't increase your security or privacy enough to warrant using, especially given the time it. Also, your isp can see that you're using tor, which may make it suspicious or make you a target. Tor is a free browser that will.
- Dapatkan link
- X
- Aplikasi Lainnya
Postingan Populer
Queen Bee Miraculous - Queen Bee edits | by Joceline | Miraculous Amino - Miraculous ladybug with chloe queen bee new transformation coloring book.
- Dapatkan link
- X
- Aplikasi Lainnya
Amc Stock Value - AMC Stock Sale Raises $587 Million as Meme Traders Buy Shares : Amc entertainment stock quote and amc charts.
- Dapatkan link
- X
- Aplikasi Lainnya
Komentar
Posting Komentar